Malware Simulation
Malware Simulation in Cyber Scoring Rigorous testing of cybersecurity defenses with lifelike scenarios, enabling proactive identification of vulnerabilities, enhancing resilience, and ensuring robust protection against real-world malware threats in dynamic digital environments.
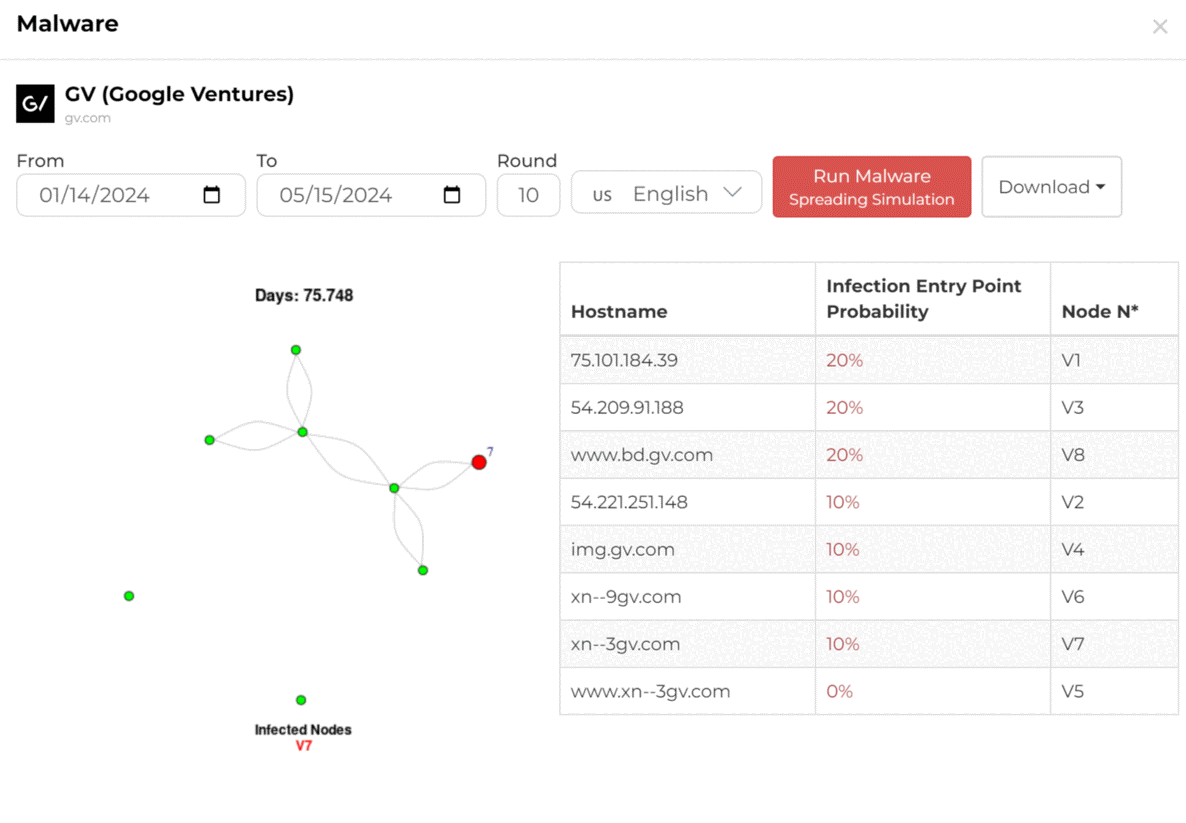
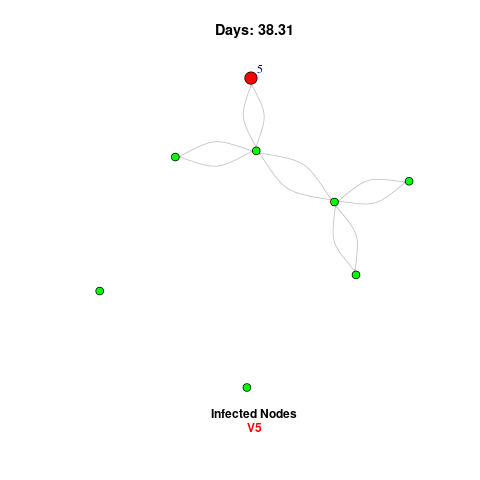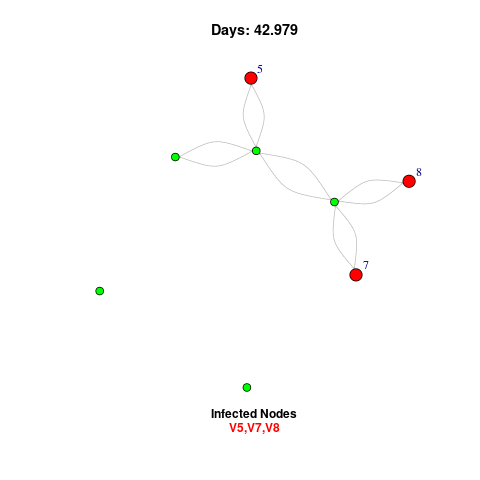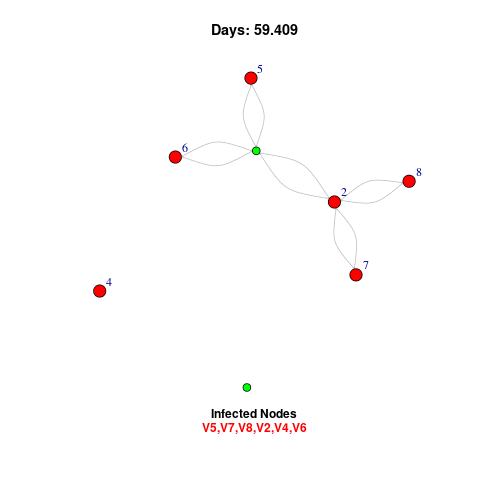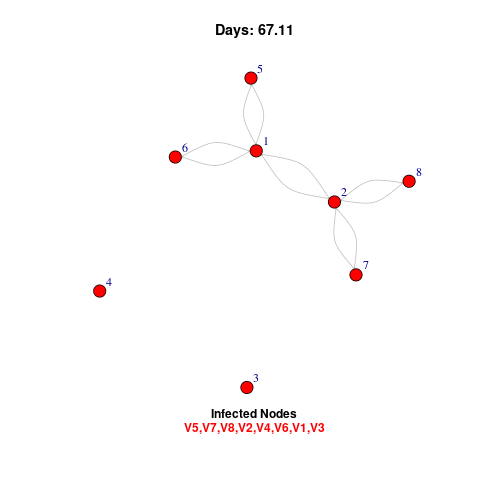
Node Identification
Node identification detects vulnerable points in a network by flagging infected nodes for action. Key strategies include isolating compromised nodes, applying security patches, and monitoring traffic for unusual behavior. The visual shows infected nodes in red and secure ones in green, helping quickly identify risks.

Hostname Infection Status
Track the infection status of each hostname in real-time to keep your network secure. Our system provides instant risk assessments, allowing for rapid response to threats. Stay proactive and protect your infrastructure with continuous monitoring and timely updates to prevent potential breaches.

Matrix Impact Score Evaluation
Evaluate the impact score of each system connection by analyzing critical factors such as security, privacy, and compliance. This prioritizes security measures, focusing on high-risk areas to safeguard system integrity and mitigate potential vulnerabilities effectively.
 Login
Login