Vulnerability Prioritizer
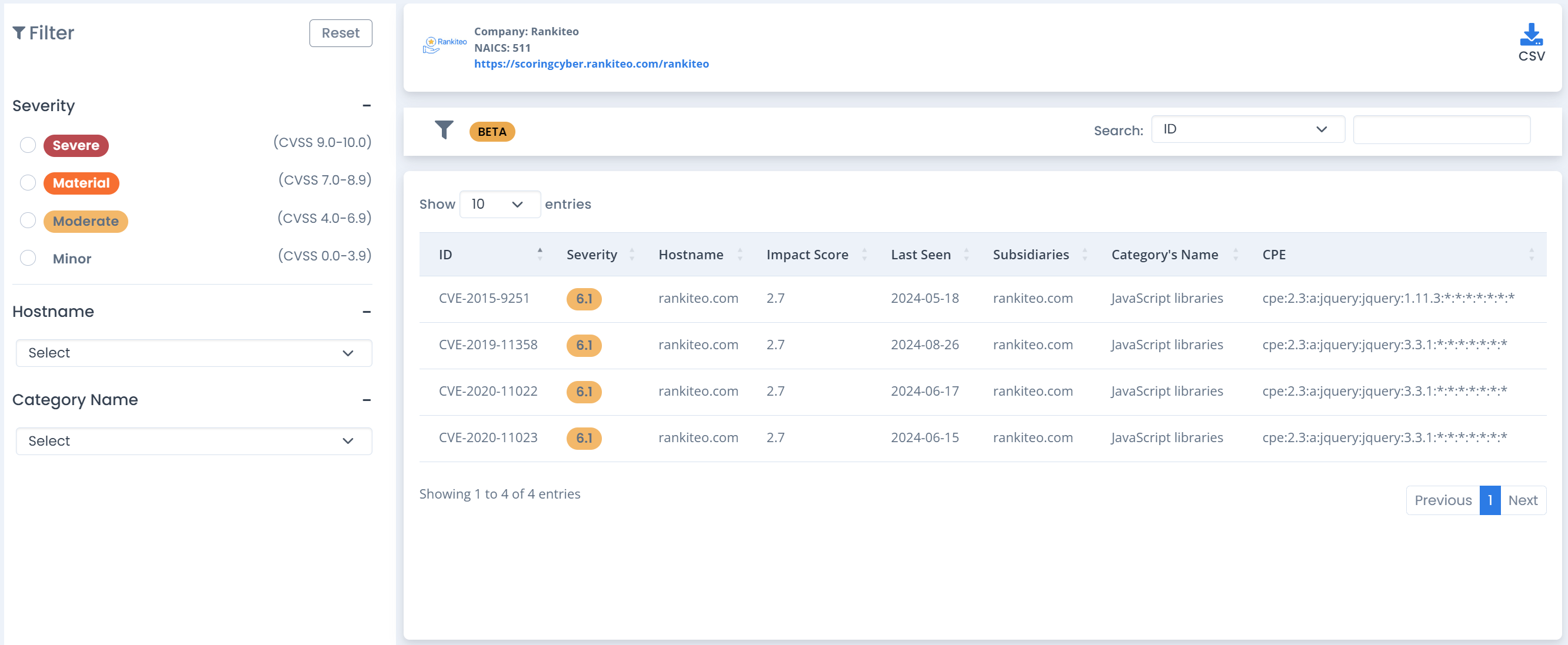
Our platform's Vulnerability Detection identifies and scores live cybersecurity threats, while the Vulnerability Catalog provides a detailed database of known vulnerabilities with severity ratings, aiding in strategic, informed defense and enhancing your company's resilience against cyber attacks.
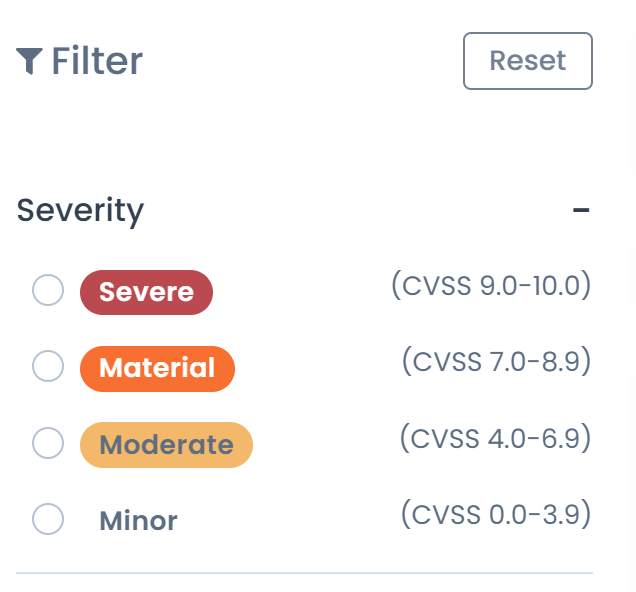
Severity Classification
The vulnerabilities currently lack explicit severity scores. However, there is an available filter option that allows users to sort and view vulnerabilities based on their criticality. This filtering capability enables users to effectively categorize and prioritize vulnerabilities according to their severity levels, even in the absence of specific numerical scores. By utilizing this feature, users can focus on addressing the most critical vulnerabilities first and manage their security efforts more efficiently.
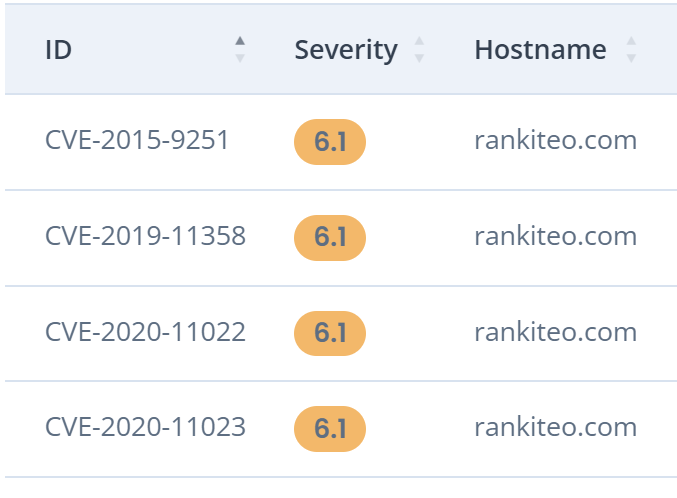
Average Severity Score
To understand the overall threat level, we calculate the average Rankiteo Severity score for all cataloged vulnerabilities. This average provides a snapshot of the general risk posed by these vulnerabilities. By evaluating this score, we can gauge the overall severity and prioritize which vulnerabilities require immediate attention. This helps in allocating resources effectively and addressing the most critical issues. Overall, it gives a clear indication of the threat landscape we are dealing with.
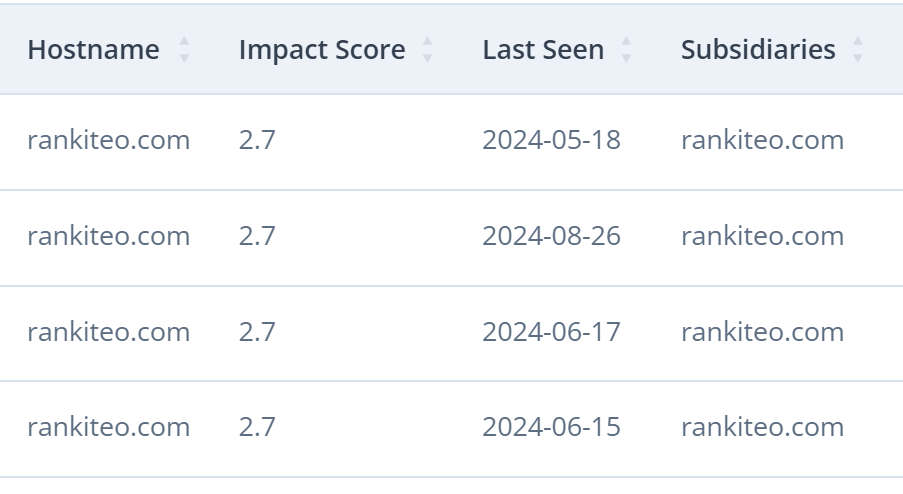
Impact Scoring
It quantifies the severity of each vulnerability, helping organizations make informed decisions about resource allocation and remediation. By assessing factors like potential damage, exploit likelihood, and operational disruption, this system prioritizes vulnerabilities based on their impact. This approach ensures that critical issues are addressed first, optimizing both security and resource management.
 Login
Login