Threat and Risk Intelligence
Our platform offers real-time insights into the latest cyber threats, helping organizations proactively identify and mitigate risks. With advanced analytics and continuous monitoring, it delivers actionable intelligence, enabling swift responses to potential vulnerabilities. Protect critical assets and stay ahead of evolving threats with our comprehensive threat detection and risk management tools.

Real-Time Threat Visibility
The platform provides an integrated, real-time view of all current threats across your digital environment, empowering security teams to react swiftly to emerging dangers. By visualizing threats as they unfold, users gain an immediate understanding of where vulnerabilities lie, what assets are at risk, and the overall security posture of their organization. This proactive visibility enables faster decision-making, reducing the likelihood of successful attacks and minimizing potential damage.
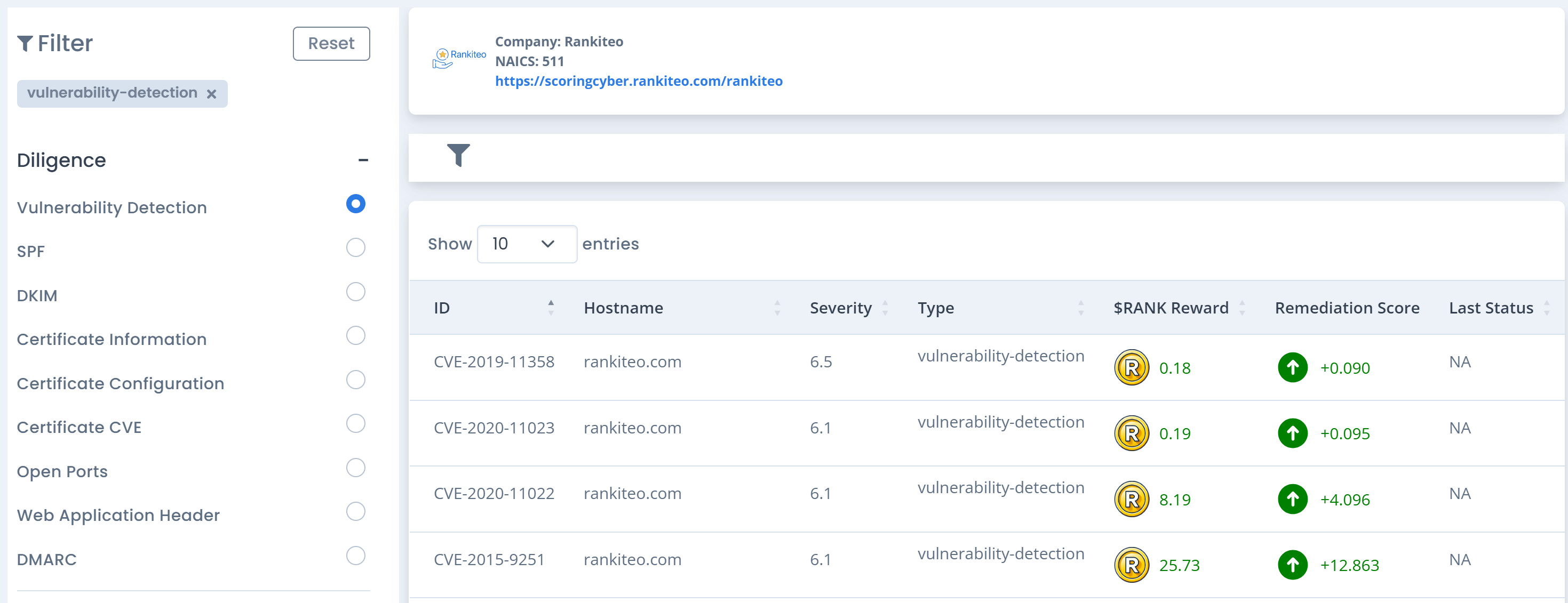
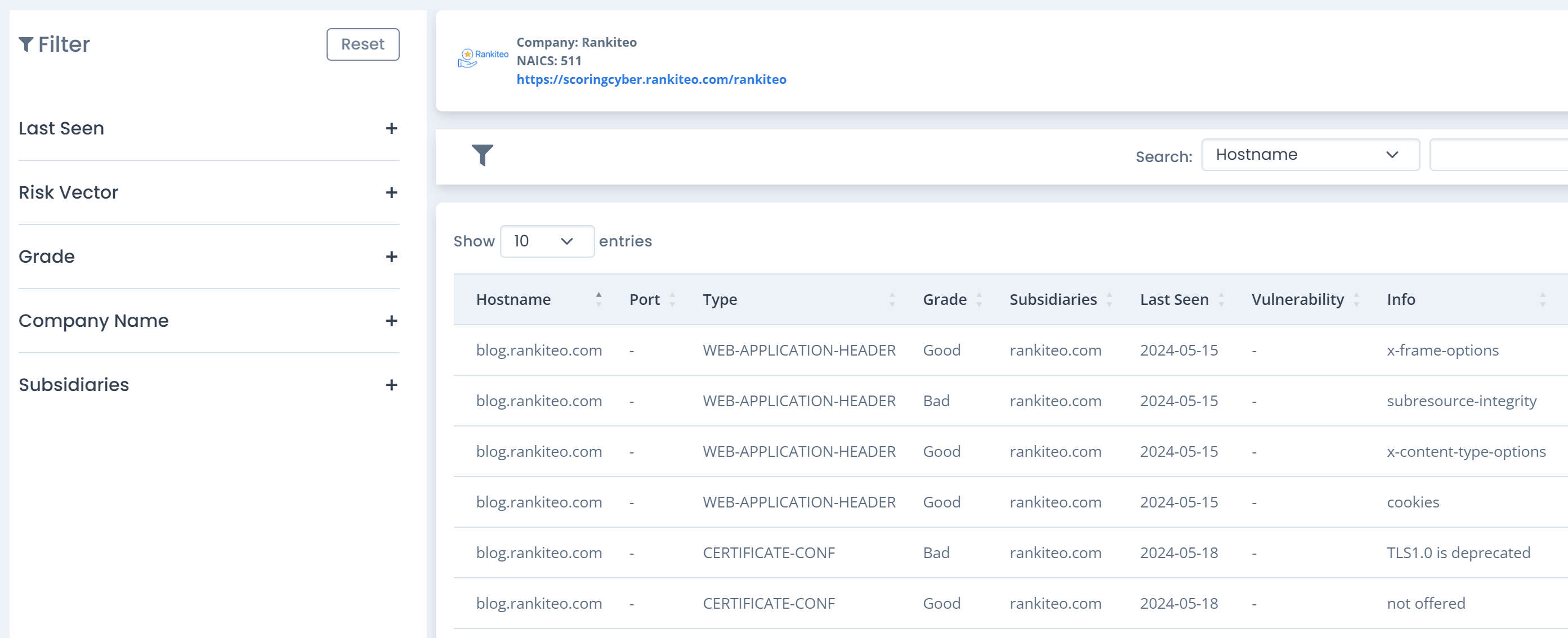
Vulnerability Management
Focuses on the automated identification of vulnerabilities across systems, using advanced scanning tools to detect weaknesses. It incorporates the latest threat intelligence to prioritize risks, providing detailed remediation recommendations like patches and configuration changes. This approach helps organizations reduce their attack surface, enhance security, and maintain compliance with evolving industry standards.
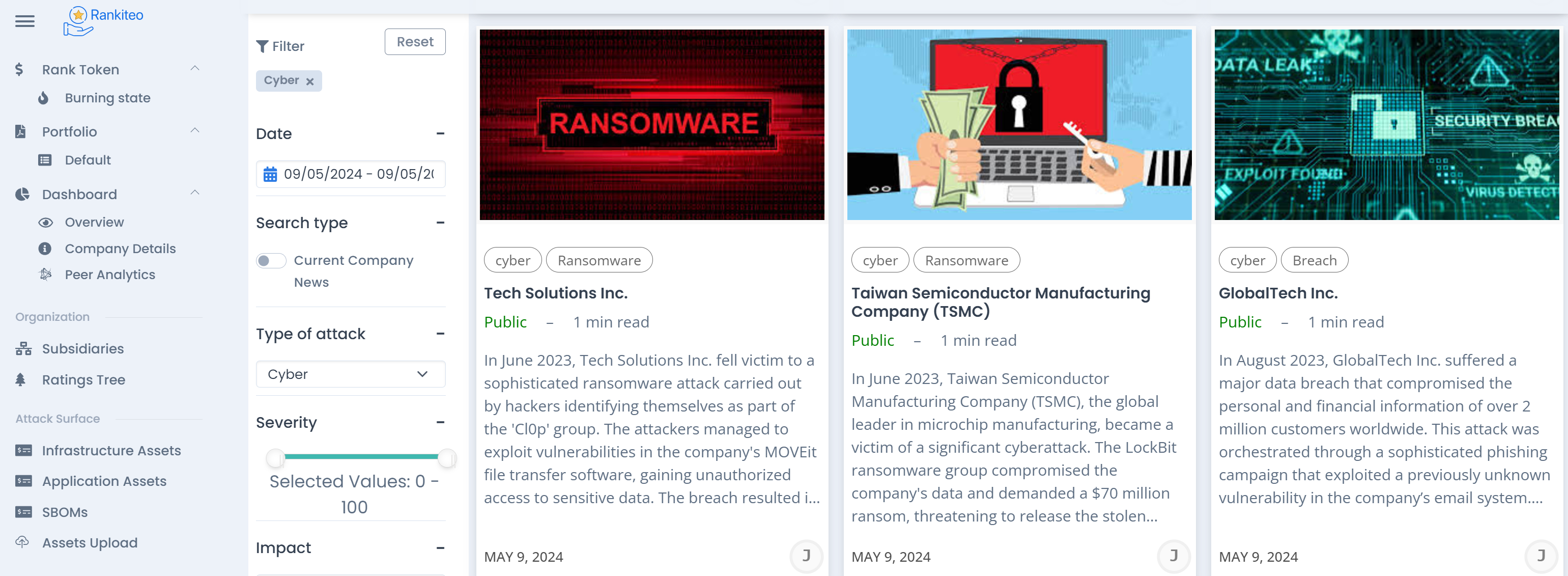
Global Threat Trends
This section provides real-time updates on the evolving cyberthreat landscape. It includes comprehensive intelligence reports sourced from across industries, highlighting emerging threats such as ransomware, phishing campaigns, data breaches, and zero-day vulnerabilities. The platform analyzes threat vectors in various regions, industries, and asset types, offering users predictive insights into potential risks. Users can access detailed reports on global incidents, risk levels, and mitigation strategies, allowing for proactive security measures based on the latest intelligence.

Malware and Ransomware Protection
The simulation maps how an attack propagates through a network, highlighting vulnerable nodes and identifying weak points. It emphasizes the need for protective measures such as file analysis, sandboxing, and anomaly detection to prevent malware and ransomware attacks from infiltrating and spreading.
 Login
Login